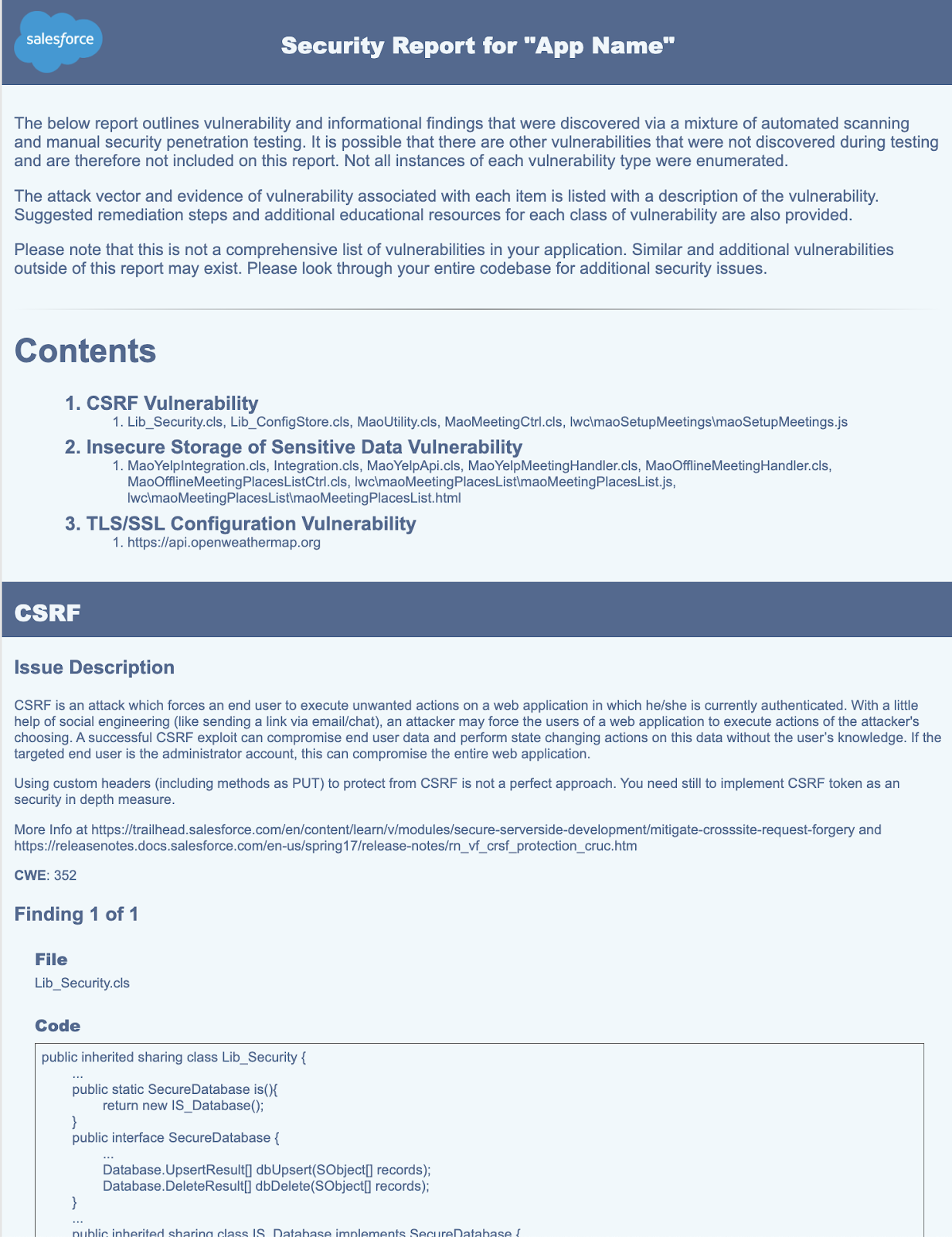
Mastering the AppExchange Security Review: Your Strategic Guide to Approval
Passing the Security Review is mandatory to launch an app on Salesforce's AppExchange. This thorough process ensures your app adheres to strict security standards, protecting the platform's ecosystem.
This article breaks down Salesforce AppExchange Security Review process, highlighting its importance, steps required, and tips for boosting your app's security and compliance.
Key Takeaways
The Salesforce AppExchange Security Review is a rigorous process to ensure app safety, involving a detailed submission that is vetted for common web vulnerabilities and Salesforce-specific security concerns.
Developers must prepare extensively for AppExchange security review. This includes running security scanners to detect vulnerabilities and addressing shared security issues such as insecure authentication, access controls, and secure data storage practices.
Post-submission, the security review typically takes 6-8 weeks, with developers needing to act on feedback for any identified issues. Successful approval leads to eligibility to publish on the Salesforce AppExchange, with support available through Salesforce resources and tools.
Understanding Salesforce AppExchange Security Review
Here are some key aspects to better understand AppExchange Security Review:
Importance: Safeguards the AppExchange by ensuring all apps are secure and reliable, preventing data breaches, and upholding security standards.
Process: Apps undergo a thorough security assessment by the Salesforce Security team, fortifying them against potential security threats and verifying their safety measures.
Analogy: Like municipal inspection teams monitor safety and health standards in a city, an AppExchange security review team meticulously assesses Salesforce apps for vulnerabilities.
Procedure: App developers submit their code for evaluation. Security review teams try to breach app security, finding possible vulnerabilities. If passed, the app is ready for AppExchange listing.
Outcome: Ensured high protection across the Salesforce ecosystem, making the marketplace safer for enterprises of Fortune 500 scale.
AppExchange security review sample
Navigating the AppExchange Security Review Process
Before Salesforce AppExchange security review submission, ensure that:
All terms, conditions, and directives are fully read and understood.
You’ve gone through all the available Security Review Resources to examine potential security issues.
You're enrolled in the AppExchange Partner Program and have a valid distribution agreement.
You satisfy every approval requirement available in the Submission Wizard via the Partner Community Publishing Console.
Pre-Review Preparation Checklist
Here’s what to include in your preparation checklist:
Internal Review: Conduct a thorough investigation of your application's code for security vulnerabilities, like a detective examining evidence.
List Dependencies: Compile a comprehensive list of all external dependencies and services used by your application that are essential for the security review process.
Documentation Package: Prepare detailed documentation covering all security aspects of your application, akin to assembling a case file for court.
Key Security Scanning Tools for Salesforce Applications
Explore some key aspects related to Salesforce’s recommended security scanning tools:
Salesforce-Endorsed Scanners: Salesforce recommends the Force.com Security Source Scanner, Chimera, and ZAP for inspecting your application's codebase and external interactions and identifying vulnerabilities.
Functionality: These scanners serve as a dedicated team of security experts adept at uncovering potential threats or weaknesses in your application.
Detection Capabilities: Designed to spot various security issues, including Cross-Site Scripting (XSS), SOQL/SOSL Injection errors, access control problems, susceptibility to CSRF attacks, and inappropriate redirects.
Integration and Usage: This can be used via command-line or integrated into CI/CD workflows, enhancing development processes with security checks.
Scanning and Simulation Tools: ZAP facilitates attack simulations on web applications to highlight breach-prone areas, while the Force.com Security Source Scanner offers pre-set scan profiles for comprehensive analysis.
Advanced Analysis Engines: Utilize sophisticated engines like PMD, ESLint, and RetireJS for in-depth code examination, targeting problematic code segments efficiently.
Interpreting Scanner Reports
We covered this topic in fine detail in the blog post below👇.
Addressing Common Security Vulnerabilities
While developing an AppExchange solution, it’s crucial to keep a vigilant eye on common security vulnerabilities such as:
Insecure Authentication/Access Control: Problems with authentication and access mechanisms.
Insecure Direct Object References: Risks from improperly secured direct object references.
Function-Level Access Controls: Lack of sufficient controls at the function level.
Security Misconfigurations: General settings that compromise security.
Record-sharing infractions: Issues with improper record sharing.
CRUD/FLS Vulnerabilities: Concerns with Create, Read, Update, Delete/Field Level Security on the Salesforce platform.
SOQL Injection Attacks: Risks from dynamic SOQL queries not validating user input properly, leading to potential unauthorized data access or changes.
If you’ve already found any of these vulnerabilities in your code, don’t shy away. Hire AppExchange Developers at Concretio.
Simplified Security Practices for Customer Data
Follow these security-best practices to protect customer data:
Secure Storage: Use secure environments like Partner Developer Edition orgs for testing.
Field-Level Security: Utilize the stripInaccessible method to protect data fields.
Permissions Checks: Use Schema.DescribeSObjectResult for object and field permissions.
SOQL Queries Security: Include 'WITH SECURITY_ENFORCED' for enhanced query security.
Custom Record Sharing: Implement Apex-managed sharing for tailored access control.
Implementing Access Control in Apex Code
Some key tips to implement access control in Apex code:
Default Behavior: Apex code executes in system mode by default, bypassing user permissions and sharing rules.
'With Sharing': Enforces record-level security by applying the current user's permission-defined sharing rules.
'Without Sharing': Allows Apex classes to operate under system mode, ignoring user-specific sharing settings.
'Inherited Sharing': The Apex class inherits access controls from its parent class, adhering to established permission levels.
Control Over Data Access: These keywords ('with', 'without', 'inherited') offer precise control over data accessibility within your app, ensuring only authorized users can access specific records.
Creating a False Positives Document for AppExchange Security Review
While creating a False positives document:
Justify Each False Positive: Provide detailed explanations for each false positive, proving why it doesn't affect your application's security.
Provide Evidence: Use code snippets, configurations, or screenshots to support your claims.
Categorize False Positives: Organize false positives by their nature to simplify the review process.
Focus on Essential Justifications: Highlight only the necessary information that proves the findings are harmless.
Keep the Document Updated: Regularly update the document to reflect changes in your application, ensuring it remains relevant for future security assessments.
Read More >
1. Document Your Responses to False Positives
2. False positive Documentation Template
Utilizing Support Tools for Salesforce AppExchange Security Review
Follow these Salesforce support tools to ace AppExchange security review:
Salesforce Trailhead: Access trails and modules on optimal security practices for quick learning.
Secure Coding Guidelines: Essential for developers to identify and fix potential security issues.
Office Hours with Experts: Schedule time with Salesforce professionals for insights on security scans and addressing security concerns.
SFDX-scanner Tool: A key resource for AppExchange developers preparing applications for the Salesforce Security Review.
Trailhead Modules for Mastering Security Practices
Salesforce Trailhead offers detailed modules on security best practices and secure application development. This includes:
Essential Modules:
Essential Preparation: Documentation and User Credentials
Just like a passport and visa are crucial for international travel, thorough documentation and user credentials are vital for a smooth AppExchange security review.
Documentation: Acts as your app's passport, detailing its functionalities and data security measures.
Dual Purpose: Serves both as a review tool and as instructional material for customers.
Access Credentials: Required for a test environment to allow hands-on evaluation by Salesforce security experts.
Preparation Tip: Ensure comprehensive preparation of documentation and user credentials before submitting your app for review.
Steps to Submit Your App for AppExchange Security Review
Simple steps for Salesforce AppExchange security review submission:
Create a Partner Community Account: Your gateway to manage your Salesforce ISV partnership and access various tools.
Use the Environment Hub: Helps in managing Salesforce orgs and streamlines development.
Assemble a Beta Package: An initial version before the final managed package.
Enable Namespace: Coordinate with the packaging of your application.
Conduct Rigorous Testing: Ensure your 'Golden Package' is flawless and ready.
Create a Partner Community Listing: This is an essential step before submitting your app.
Security Review Costs: Be aware of fees for monetized applications; free apps are assessed without charge. Read our blog > Security Review Cost FAQs
Approval and Listing: Once passed, your app is listed on The Salesforce AppExchange for global access.
What Happens After AppExchange Security Review Submission?
Salesforce AppExchange Security review process
Review Timeline: Security review typically takes 6 to 8 weeks. Resubmissions follow the same timeframe, potentially longer during peak periods like Dreamforce.
Feedback on Vulnerabilities: If issues are found, you'll receive an email with a detailed report and guidelines for fixes.
Approval Notification: Upon approval, you'll get instructions via email on how to publish your app.
Possible Outcomes: Either approval confirmation or advice on necessary corrections.
Expedited Updates: Once initially approved, subsequent updates to your app may receive quicker approvals.
Responding to AppExchange Security Review Outcomes
View as an Opportunity: I know it's very tough to do so, but I consider the security review as a chance for feedback and improvement, not just a pass/fail test. Imagine your customers identify those security gaps 😱, it will be an immense shame.
Address Vulnerabilities: If issues arise, resolve them and resubmit your app for another review. Don’t forget to consult with a Salesforce PDO partner if there are too many issues or if there’s something you are unable to deal with on your own.
Confirmation of Approval: After resolving security concerns, you'll receive an email from the Salesforce Security team endorsing your app.
Growth and Learning: Whether your app passes smoothly or encounters challenges, each step of the process contributes to your growth and knowledge.
Summary
In this blog, we covered:
Process Overview coverage: From understanding the importance of the security review to submission and response strategies.
Security Scanning Tools: Explored essential tools for identifying vulnerabilities.
Addressing Vulnerabilities: Highlighted how to tackle common security issues.
False Positives Document: Learned crafting techniques for a document to clarify non-issues.
Leveraging Salesforce Resources: Discussed how additional resources can aid in preparation.
Documentation and Credentials Preparation: Emphasized the importance of thorough documentation and providing necessary access credentials.
Frequently Asked Questions
-
Salesforce is a platform trusted by some of the world's biggest companies (Fortune 500). This means the data flowing through Salesforce apps is critical for running those businesses.
Unlike app stores for phones, where breaches might expose personal information, security breaches on the Salesforce AppExchange could compromise vital business data. That's why a robust security review process is essential. -
Typically, the duration for a Salesforce security review spans between four to six weeks. This timeframe may fluctuate based on the quality of the submission presented for the security review.
-
To successfully navigate a security review within Salesforce, you must thoroughly test your developed application. Testing should include creating robust security-focused code and utilizing resources like the Force.com Code Scanner Portal.
-
The security review on the AppExchange meticulously inspects your product’s protection of customer data, confirming that it aligns with Salesforce’s rigorous security criteria. This examination aids in detecting and mitigating any possible vulnerabilities within your solution.
-
You should use specific security scanners like the Force.com Security Source Scanner, Chimera, and ZAP to detect vulnerabilities within your app’s code and external services. Salesforce recommends these tools for security scanning.
Related Readings
Salesforce AppExchange Security Review Fees- FAQs Answered
Watch Video On Insider's Guide To Appexchange Security Review
Watch Video On Tips And Tricks To Pass The Salesforce Security Review Process- By Salesforce
Lets Talk!
Drop a note with your queries to move forward with the conversation 👇🏻